ABSTRACT:
Benefited
from cloud computing, users can achieve an effective and economical approach
for data sharing among group members in the cloud with the characters of low
maintenance and little management cost. Meanwhile, we must provide security
guarantees for the sharing data files since they are outsourced. Unfortunately,
because of the frequent change of the membership, sharing data while providing
privacy-preserving is still a challenging issue, especially for an untrusted
cloud due to the collusion attack. Moreover, for existing schemes, the security
of key distribution is based on the secure communication channel, however, to
have such channel is a strong assumption and is difficult for practice. In this
paper, we propose a secure data sharing scheme for dynamic members. Firstly, we
propose a secure way for key distribution without any secure communication
channels, and the users can securely obtain their private keys from group
manager. Secondly, our scheme can achieve fine-grained access control, any user
in the group can use the source in the cloud and revoked users cannot access
the cloud again after they are revoked. Thirdly, we can protect the scheme from
collusion attack, which means that revoked users cannot get the original data
file even if they conspire with the untrusted cloud. In our approach, by
leveraging polynomial function, we can achieve a secure user revocation scheme.
Finally, our scheme can achieve fine efficiency, which means previous users
need not to update their private keys for the situation either a new user joins
in the group or a user is revoked from the group.
AIM
The
aim of this paper is to propose a secure data sharing scheme for dynamic members.
SCOPE
The
scope of this paper tends to our scheme can achieve fine efficiency, which
means previous users need not to update their private keys for the situation
either a new user joins in the group or a user is revoked from the group.
EXISTING SYSTEM
A
secure access control scheme on encrypted data in cloud storage by invoking
role-based encryption technique. It is claimed that the scheme can achieve
efficient user revocation that combines role-based access control policies with
encryption to secure large data storage in the cloud. Unfortunately, the
verifications between entities are not concerned, the scheme easily suffer from
attacks, for example, collusion attack. Finally, this attack can lead to
disclosing sensitive data files
presented a practical and flexible key management mechanism for trusted collaborative computing. By
leveraging access control polynomial, it is designed to achieve efficient
access control for dynamic groups. Unfortunately, the secure way for sharing
the personal permanent portable secret between the user and the server is not
supported and the private key will be disclosed once the personal permanent
portable secret is obtained by the attackers. proposed a privacy preserving policy-based
content sharing scheme in public clouds.
However, this scheme is not secure because of the weak protection of commitment in the phase of
identity token issuance.
DISADVANTAGES
- Unfortunately, because of the frequent change of the membership, sharing data while providing privacy-preserving is still a challenging issue, especially for an untrusted cloud due to the collusion attack.
- The security of key distribution is based on the secure communication channel, however, to have such channel is a strong assumption and is difficult for practice.
PROPOSED SYSTEM
In this paper, propose a secure
data sharing scheme for dynamic members. Firstly, we propose a secure way for
key distribution without any secure communication channels, and the users can
securely obtain their private keys from group manager. Secondly, our scheme can
achieve fine-grained access control, any user in the group can use the source
in the cloud and revoked users cannot access the cloud again after they are
revoked. Thirdly, we can protect the scheme from collusion attack, which means
that revoked users cannot get the original data file even if they conspire with
the untrusted cloud. In our approach, by leveraging polynomial function, we can
achieve a secure user revocation scheme. Finally, our scheme can achieve fine
efficiency, which means previous users need not to update their private keys
for the situation either a new user joins in the group or a user is revoked
from the group.
ADVANTAGES
- Our scheme is able to support dynamic groups efficiently, when a new user joins in the group or a user is revoked from the group, the private keys of the other users do not need to be recomputed and updated.
- Our scheme can achieve secure user revocation, the revoked users can not be able to get the original data files once they are revoked even if they conspire with the untrusted cloud.
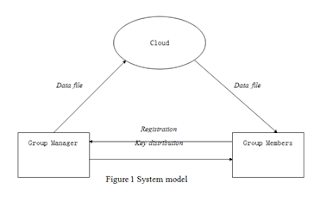
SYSTEM ARCHITECTURE
SYSTEM CONFIGURATION
HARDWARE REQUIREMENTS:-
· Processor - Pentium –III
·
Speed - 1.1 Ghz
·
RAM - 256 MB(min)
·
Hard
Disk - 20 GB
·
Floppy
Drive - 1.44 MB
·
Key
Board - Standard Windows Keyboard
·
Mouse - Two or Three Button Mouse
·
Monitor -
SVGA
SOFTWARE REQUIREMENTS:-
·
Operating
System : Windows
7
·
Front
End : ASP.NET and C#
·
Database
: MSSQL
·
Tool :Visual Studio
REFERENCE:
Jian
Li, Ruhui Ma, Haibing Guan, “TEES: AN EFFICIENT SEARCH SCHEME OVER ENCRYPTED
DATA ON MOBILE CLOUD”
No comments:
Post a Comment